
Our Cyber Threat Intelligence team here at Hitachi Systems Security collects, analyzes and assesses threats for our global client base. Our goal is to identify potential cyber threats and provide our clients intelligence and recommendations concerning how to manage and minimize these threats.
Essentially, our CTI group (Cyber Threat Intelligence) team tracks global trends, eCrime and hacktivist adversaries and deliver profiles of each actor to our client’s IT security team so they can understand attackers’ motivation and proactively defend against their tactics, capabilities, and tradecraft — the why, what, and how of a potential attack.
Based on the substantial number of threats we have analyzed over the past year or so, we can up with the five that we feel are not only the most significant threats, but also the threats that are still growing in sophistication and number. Hope you find the post helpful, interesting, and enjoyable!
Hacktivism is not a new phenomenon. Groups such as Anonymous and Wikileaks and individuals like Edward Snowdon have demonstrated how cyber can impact activism. There is more than one way that hacktivists are used; web defacement, social engineering, doxxing, leaking confidential information are several ways we’ve seen in the past, however what if approaches became more destructive. What if the goal was for more political exposure? Perhaps analogous to chaining oneself to a tree to protect it from destruction. Why not attack a company by tearing it down in the if their behavior is not in line with the values of the Ecohacktivists that have an Eco-friendly agenda?
The new generation of environmental/eco-hacktivists know how to take advantage of social media tools to promote the causes for which they advocate. This is likely the new reality in 2023. Last year, we saw environmental hacktivists not only targeting mining and oil companies in Central and South America, but also government websites. For example, the hacktivist group Guacamaya (macaw parrot in Mayan), claims to have hacked a Colombian government agency, or the Ecuadorian state-owned mining company ENAMI EP, Quiborax.
Climate Hacking has been used to help organizations to help fight global warning. Universities such as MIT have journals discussing how technology can help save the planet from devastating effects of global warming. However, even good innovations can also be use negatively.
The goal of ecohacktivists is expose the companies and government entities that are conducting behavior that the ecohacktivists find damaging to the climate, victim countries and people that are harmed by these organizations. They want everyone to know how the organizations operate, their actions, their profits, and their position that the company will pursue profits no matter the damage they cause to their victims. The new generation of young adults are known to be more politically woke than ever and want to stand against big corporations to fight climate change, gun reform, and women’s right to choose. It may just be a matter of time that more of these young adults combine their ideology and their technological skills to create a new class of hacktivism.
Lazarus Group also known by other monikers such as Guardians of Peace or Whois Team is a cybercrime group made up of an unknown number of individuals run by the government of North Korea. Lazarus is a North Korean Advanced Persistent Threat (APT) and state-sponsored malware group that has been active since at least 2009. Over the years, Lazarus or APT 38 is responsible for countless attacks and subsequent damage. According to research by Talos Intelligence, Lazarus leveraged the Log4j vulnerability known as Log4Shell to compromise internet-exposed VMware Horizon servers. They used this vulnerability to establish a presence on the victims’ network and to deploy malware to facilitate persistent access to systems.

In addition, some of their other more known attacks include the cyber-espionage campaign Operation Troy from 2009-2012, the Sony Pictures attack in 2014 and the devastating WannaCry ransomware attack of 2017. The group is known for having a wide variety of tools at their disposal and the ability to adapt their tactics to exploit their targets.
Lazarus is not a one trick pony; they are versatile, diverse in their attacks and based on their recent malware strains, constantly evolving. Depending on their target, the APT group can adapt their modus operandi to ensure a successful attack. Consequentially, their target needs to consider their entire infrastructure and protect their attack surface from all angles. They need to further hope that criminal group does not find and deploy zero-day attacks.

Stepping back in time just a bit, last year the group developed a new version of a crypto-stealing malware known as AppleJeus. Threat intelligence in the cyber community suggests the aim of this tool was to steal funds for Kim Jong-un’s weapons program. According to FBI, Lazarus is said to be responsible for the theft of $620 million in Ethereum crypto coins reported last year.
Lazarus has been ranked among the most dangerous groups according to the FBI. The identity behind the group is well protected. Even after years and countless attacks little is known about the leadership or its members. For example, Park Jin Hyok is a North Korean hacker wanted by the FBI for being part of the Lazarus group, however North Korean denies his existence.
Because of the length of time they have been commiting cyber crime, we can assume that many of the individuals who originally formed the group have since left. The group seem to be well protected and their aninimity guarded by the government of North Korea which provides them ample protection and freedom to conduct attacks, particularly against the west.
Humans have always been the best defense yet the worse risk in cybersecurity. Humans’ weakness has been leveraged by threat actors for years through social engineering and other attacks. However, people also represent on the the most damaging element of cyber threats due to their ability to conduct attacks from inside the organization. Insider threat attacks are typically the most damaging attacks financially as insiders often know where sensitive information is stored.
Human error represents a significant risk to any organizations. Human error includes weak passwords, unsecure devices accessing sensitive information, BYOD security issues and yes, even finding USB drives in a parking lot and plugging them into their corporate device. This type of poor cyber hygiene has led to millions of successful cyberattacks over the years.
However, the most destruction threat that is emerging is the cyber insider threat. Criminal groups are now offering money in exchange for employees or ex-employees’ information about their organizations. Information on software used, credentials, vulnerabilities and other sensitive information is targeted by groups that can use this information to launch an attack.
Further, for an angry employee, this represents an opportunity to make money and take revenge on their employer with limited risk of detection. Paying your employees their worth, being good managers and providing quality working conditions will lead to lower disengagment and will likely lower your risk of an insider attack.
The opportunity for IT security is that humans are also an organization’s best defense against cyber threats; and they are emerging as an offensive force against cyber threats. Security is everyone’s responsibility. Organizations need not only rely on the cybersecurity units or IT department, they should also rely on employees and management. Employees outside of information technology have a crucial role in limiting the risk of a cyberattack. Each time a phishing attack fails because an employee recognized an illigetimate link or nefarious PDF and did not fall victim to it, they have protected their organisation; and likely saved their organization downtime and millions of dollars.
Cybersecurity technology, tools and products are certainly effective in improving the security posture of an organization, however, companies need their employees to deploy those tools properly, monitor for abnormalities and most importantly understand how to recognize social engineering attacks.
LockBit is a new ransomware attack in a long line of extortion cyberattacks. Formerly known as “ABCD” ransomware, it has since evolved into a unique threat within the scope of extortion malware. LockBit is a subclass of ransomware known as a ‘crypto virus;’ meaning its intent is to lock files on the system it attacks for the purpose of collecting a ransom for decryption. It focuses mostly on enterprises and government organizations rather than individuals.
Lockbit first appeared around 2019; Lockbit 2.0 was introduced in January 2021 and finally Lockbit3.0 appeared in March of last year. The Lockbit family is said to be part of the LockerGoga and MegaCortex malware family. According to ID Ransomware, a free service to identify ransomware, there exist 928 different pieces of ransomware, however Lockbit is among the most prolific and damaging.
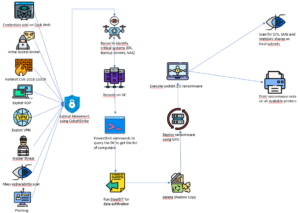
Lockbit3.0 is a leakware ransomware-as-a-service (RaaS). RaaS is a business model whereby affiliates who lack technical skills to develop their own ransomware variant can buy a ready-made attack simply by downloading the malware typically found and bought on the Dark Web. Leakware also known as double extortion or doxware differs from traditional ransomware by threatening to publish the data rather than simply locking it on the victim’s system. Although they were not the first group to start executing leakware attacks, the Lockbit family has been very prolific and able monetarize their attacks., resulting in millions in ransomware payments.

In addition, Lockbit3.0 was the first group to introduce the first bug bounty program. On their Lockbit website, they wrote, "we invite all security researchers, ethical and unethical hackers on the planet to participate in our bug bounty program.” The amount of the bounties ranges from $1,000 to $1 million. In addition, the group went further and offered to pay bounties for new ideas on how to improve their malware distribution service.
Azov ransomware is not a traditional ransomware group; their modus operandi is a little different than what is often seen. It is even debateable if they are a ransomware group or not. While Azov is disguised as ransomware, many in the cyber research community determined that the malware is a wiper intended for maximum data destruction. There were no signs of data exfiltration, network activity or monetary motive as with traditional ransomware groups. However, some might call them romantic, poetic or maybe a little emo. We’ll discuss this in a minute.
Our research suggests Azov is a data wiper that destroys victims’ files and infects other programs. A block of 666 bytes is overwritten with random noise data, then an identically sized block is left untouched, then another block is overwritten, and so on -- until the hard limit of 4GB is reached. Once 4GB is reached the rest of the data on the system is left untouched.

Unlike many of their criminal counterparts, in their ransom payment demand, instead of Bitcoins, they plead for help for Ukraine by directing them to security researcher’s twitter handles to recovery the files. There remains some mystery about the Azov group. Some theories exposes that the group can be trolling the cybersecurity community or that their behavior is to cover up other malicious goals.
One bit of warning we will provide is that if receive a virtual holiday or birthday card via e-mail sent as an attachment make certain it is going to a legitimate site. If you don't recognize the website and/or the greeting card comes as an attachment, leave that card unopened because the only thing found inside is likely Azov ransomware.
IT security researchers and our colleagues cannot afford to rest in the face of the growing and evolving cybersecurity threats. Fortunately, security vendors are already stepping up by developing more sophisticated behavioral AI-based tools to detect ChatGPT-generated attacks, as an example.
Unfortunately, however at the time of the post, there is no legislated protections against the criminal use of ChatGPT, but we are hoping that this may change in the future.
In the meantime, be sure to brush up on the basics. Deployment of cloud-based security solutions is non-negotiable as your first line of defense in preventing sophisticated BEC or phishing emails from reaching your end users. This should include inbound and outbound data loss prevention, email encryption, antivirus, and anti-malware.
We also recommend implementing “refresher” security awareness training in which you alert employees to the new breed of threats and their ability to deliver even more deceptive e-mails tactics, phishing, whaling, smishing and other attacks. Phishing is far and away the most used attack vector by criminals; organizations should absolutely make social engineering training their #1 cybersecurity priority.
We at in the Cyber Threat Intelligence group look forward to sharing our industry’s progress on these threats as well as those that emerge going forward. Stay safe and thank you for taking the time to read our post.