ArkAngel Platform
Security in depth is a concept that re-enforces the fact that there are no 100% secure systems. However, by utilizing a layered approach to security and introducing an AI element, threats pertaining to any organization can be brought to a minimum. To ensure a layered security approach, any organization must implement security differently.
Our Managed Security Services, offered through our proprietary ArkAngel risk management platform, are built to address your growing IT security needs and offer you the highest standard of protection with a Service Level Agreement customized to your needs and business requirements.
Superior Protection
Cost Savings
Effective Technology
Security Experts
What You Get
24/7 Threat Monitoring & Protection
Continuous monitoring of your environment • Real-time analysis and event correlation • Incident response management • 2-hour log review guarantee • Escalation of discovered threat activity • Customizable escalation process • Analysts in 4 global SOCs.
Security Posture Overview and Reporting
360-degree view of your cybersecurity maturity • Monthly executive reporting with concrete recommendations • Cybersecurity analytics tool for tracking and measurable ROI • Strategic risk management guidance • Improved alignment of security strategy and business goals and operations run smoothly.
Integration with Existing Technology
Easy integration with your existing security devices and SIEM tools • Integration with third-party security devices ( anti-DDoS, IBM AS/400 iSeries, Linux/Unix, Windows OS, etc.) • Cloud security monitoring of Office 365 logs
Analysis of Large Data Volumes
Automated log and security event correlation • Consolidated security management from one unified security portal • Customized correlation rules to filter noise and minimize false positives • Fine-tuned setting for optimized analysis • 2-hour log review guarantee.
Easy and Fast Deployment
Streamlined sensor deployment process • Optimal service efficiency within about 3 months • Smooth configuration and process efficiencies • No more lengthy configuration and fine-tuning of your SIEM (which can take up to a year in most cases).
Dedicated Team of Security Experts
Extend your in-house IT team with certified security experts • Benefit from global security expertise & threat intelligence • Get assistance and actionable recommendations from a dedicated Information Security Specialist assigned to your organization.
Save on Cost & Time
No need to buy expensive technology • No need to hire your own security staff • No time wasted reviewing your logs • Optimize your time to focus on your priorities while we take care of your security needs.
Compliance Requirements
24/7 log monitoring for PCI DSS compliance • Self-serve vulnerability scanning • Improved alignment with security control frameworks (CIS 20 CSC, NIST, ISO 27001/2, PCI DSS, HIPAA.
SOC
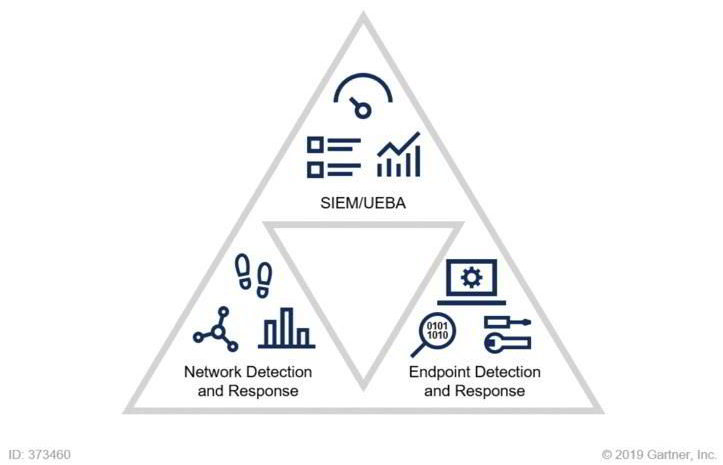
VISIBILITY TRIAD
THREE IS MORE POWERFUL THAN ONE.
TRANSFORMATION REQUIRES A CULTURE
SHIFT AT EVERY LEVEL.

professional security services
Get started today
We complement our managed security service offering with a variety of professional security services to assess your overall cybersecurity posture, align your security strategy with your business goals and provide strategic recommendations to strengthen your defenses and maximize your ROI.